You are being watched — by a silent WiFi sniffer outside of your house
We identify a new WiFi-based reconnaissance attack, which leverages the presence of commodity WiFi
devices to track users 24/7 inside private homes and
offices, without compromising any WiFi network, data
packets, or devices.
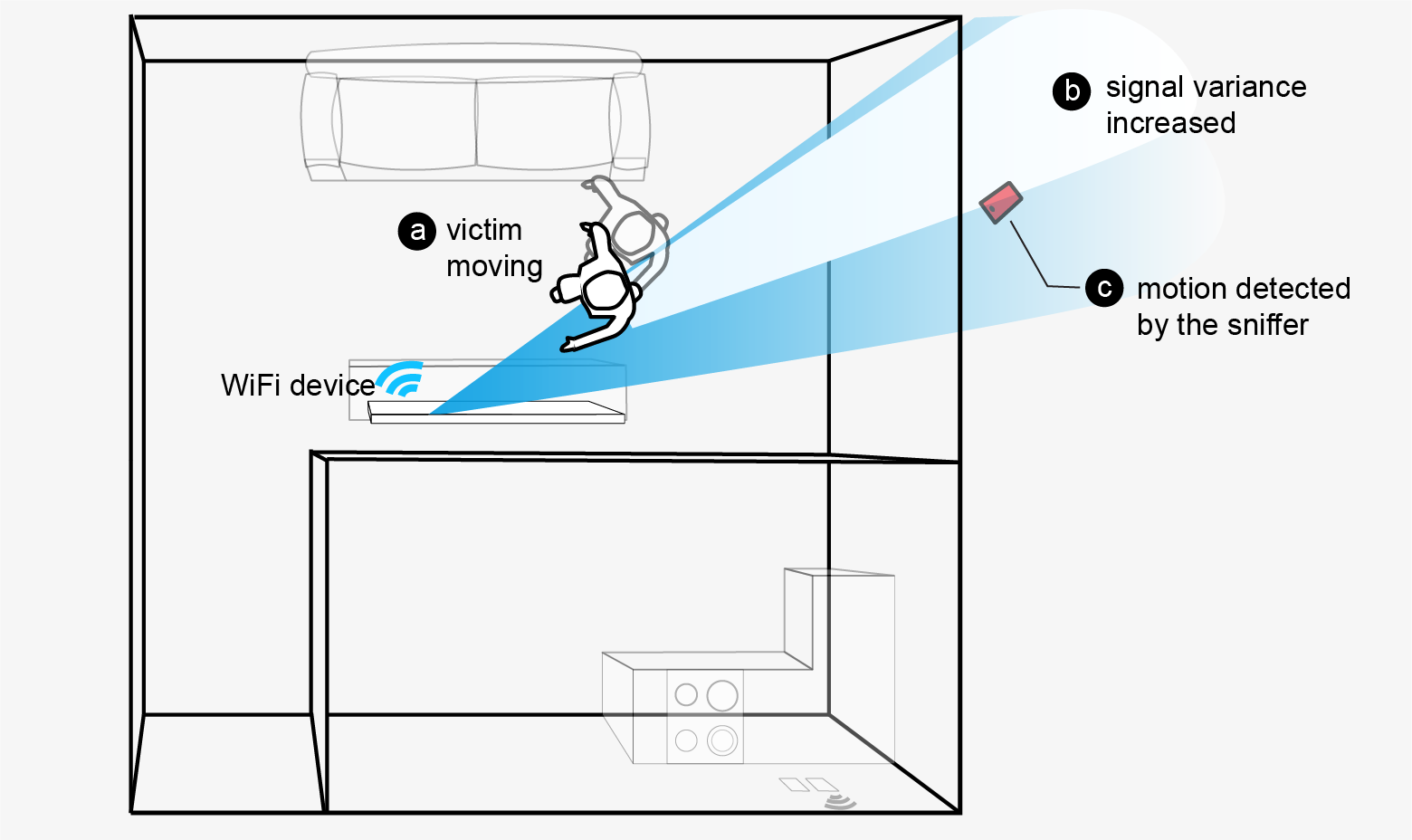
(a) victim moves inside the house, (b) human motion causes the variation in
WiFi signal strength received by the sniffer outside the house, (c) sniffer detects the human
motion based on observed signal variation.
A new WiFi-based reconnaissance attack
With near-ubiquitous deployment of WiFi-enabled smart devices (
e.g., security cameras, voice assistants, and smart appliances), our
homes and offices are filled with many WiFi
devices. The ubiquity of these devices and their sheer
density means that they will fill the air around us with radio frequency (RF)
signals, wherever we go. Unfortunately, the RF signals emitted by these devices pose a real security and privacy risk to all of us. They are constantly
interacting with (e.g., reflecting off) our bodies, carrying
information about our location,
movement and other physiological properties to anyone nearby with sufficient
knowledge and curiosity.
Our work demonstrates a new set of
passive reconnaissance attacks that
leverages the presence of ambient WiFi signals to monitor
users in their homes and offices,
even when the WiFi network, data packets, and individual
devices are completely secured and operating as expected. We show that by just
sniffing existing WiFi signals, an adversary outside of the
target property can accurately detect
and track movements of any users down to their individual rooms, regardless
of whether they are carrying any networked devices.
The resulting attacks
are cheap, highly effective, and yet difficult to detect. We implement
the attack using a single commodity smartphone, deploy it in 11
real-world offices and residential apartments, and show it is
highly effective.
Our proposed defense: AP-based obfuscation

We propose a practical defense against the silent reconnaissance attack using AP-based signal obfuscation, where the WiFi Access Point actively injects customized cover signal for its associated devices. This defense effectively creates noise to the signal measurements, such that the attacker is unable to identify change due to human motion. Our defense is easy to implement, incurs no changes to devices other than the AP, but reduces the human detection rate to 47% while increasing the false positive rate to 50%. Such ambiguity renders the attack useless in practice.
Publication & Presentation
Yanzi Zhu, Zhujun Xiao, Yuxin Chen, Zhijing Li, Max Liu, Ben Y. Zhao and Haitao Zheng. 2020. Et Tu Alexa? When Commodity WiFi Devices Turn into Adversarial Motion Sensors. In Proceedings of Network and Distributed System Security Symposium (NDSS'2020).
( Download PDF here )( Slides )
Press articles
University of Chicago PSD News: UChicago research finds external attackers can use IoT devices as motion sensors
SciTechDaily: Silent surveillance attack: How hackers can use Wi-Fi to track you inside your home


